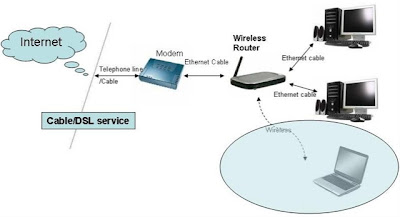
Late last year, the Institute of Electrical and Electronics Engineers (IEEE) ratified the 802.11n
wireless networking standard and this affected the small-office wireless environment.
Now we have workgroup-level 802.11n wireless routers from Buffalo Technology, D-Link Systems, Edgecore Networks and Netgear. These devices were extremely easy to set up, often requiring only the setting of an IP address to get the local computer and wireless client to communicate to each other. They all had basic router functions, such as port forwarding and a firewall. And without exception, each router had all the latest security features, such as Wi-Fi Protected Access, WPA2 and WPA2-PSK certification, in addition to Wired Equivalent Privacy 64-bit and 128-bit encryption.
Now a number of tests have been conducted comparing each of these routers.
- It was found that each of the routers performed best over a particular distance.
- Each of the routers has different strengths and is best suited for a particular implementation, also depending on the number of users and how far they need to communicate.
- The routers were also compared according to the ease of setup and making changes to the settings.
- Lastly these were compared according to their prices.
Let us discuss them one by one.
The Nfiniti Wireless-N Essential High Power Router and Access Point (WHR-HP-G300N):
It is from Buffalo Technologies, it is the smallest and lightest router in this series. At a half a pound and an inch wide, an administrator should be able to easily find a place for the Nfiniti.
It has 10/100 ports for the local-area network and wide-area network connections. The practical limit for the Nfiniti is only 100 megabits/sec. This is because the wireless traffic eventually must go out of one of the wired ports. However, the radio performed well within that constraint. It came within 3 percent of that limit with a single user going from Ethernet to wireless and within 1 percent when sending packets the other way. It did just as well in the 10-user test as in the mixed 802.11g and 802.11n test, and it lost no significant bandwidth. It had a top performance at a distance of 80 feet and an effective throughput of 6.91 megabits/sec.
The Nfiniti’s retail price of $70 is a good one, considering its radio’s power and overall ease of use. It would do well for any workgroup that has AOSS devices to connect or has a mix of 802.11g and 802.11n users.
D-Link’s DIR-825 Xtreme N Dual Band Gigabit Router:
It is from D-Link Systems and comes in a bright white case. One unique feature of D-Link is the SharePort, a USB port in the back that can be connected to a printer or external drive for access without the need of a computer. This feature is pretty useful in a workgroup environment.
D-Link has two independently controlled radios to support the 2.4 GHz and 5 GHz bands. When both are operational, the router can optimize bandwidth use by various kinds of traffic.
It is fastest at 40 feet, churning out an effective transfer rate of 13.96 megabits/sec. D-Link has set the list price for the DIR-825 Xtreme N Dual Band Gigabit Router at $200.
This router would be good for a closely grouped set of users who have a variety of media they access wirelessly.
SMCWBR14S-N3 Barricade N:
It is from Edgecore Networks and can adequately meet a workgroup’s basic wireless needs. The Barricade N has 10/100 ports for its local-area network and wide-area network connections. Its top performance was at a distance of 60 foot, producing an effective throughput of 10.68 megabits/sec.
The Barricade N SMCWBR14S-N3 from EdgeCore Networks has a list price of $60. It would perform decently for a workgroup that has basic routing needs at close distances and doesn't have too much traffic at once.
Netgear ProSafe Wireless-N VPN Firewall (SRXN3205):
It is from Netgear and they are all packed inside a sturdy metal case that you can mount on a wall or rack. The ProSafe’s antenna array has, in addition to the two dipole antennae, a patch antenna in between. That allows the ProSafe to boost the signal in the direction the antenna faces, which can be especially useful if your implementation has long-distance users in roughly the same direction. When combined with the dual radios in the 2.4 GHz and 5 GHz frequencies, you end up with a formidable broadcast device, especially at greater distances.
In addition to router and firewall functions, the ProSafe also have extensive virtual private network capability, both for IP security and Secure Sockets Layer. Its best performance is at 100 feet with an effective throughput of 3.16 megabits/sec.
Netgear is selling SRXN3205 for $259. That is a good price for a router that has all the capabilities and power of the ProSafe. It would do well in an environment with many users who are at moderate to long distances from the router.












 Let’s have a look at the following tips to format a hard drive in MAC OS X.
Let’s have a look at the following tips to format a hard drive in MAC OS X.
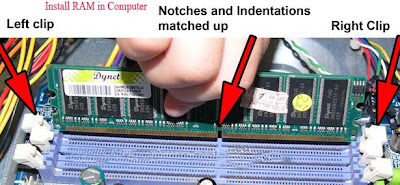
 Motherboard is basically a printed circuit board. You will find thousands of printed circuits in it which convey information or data from one part of the computer to another. A motherboard also features numerous slots and attachments so that other pc components can be attached.
Motherboard is basically a printed circuit board. You will find thousands of printed circuits in it which convey information or data from one part of the computer to another. A motherboard also features numerous slots and attachments so that other pc components can be attached.



 This silence or humming sound denotes that the drive is working properly and efficiently. But if you hear some weird noise while the drives are working, then you need to be concerned, as these weird noise denote that there is some problem while the drive is running and is not working properly.
This silence or humming sound denotes that the drive is working properly and efficiently. But if you hear some weird noise while the drives are working, then you need to be concerned, as these weird noise denote that there is some problem while the drive is running and is not working properly.